2-OXO-Butyric Acid
2-OXO-Butyric Acid is also known as Alpha-ketobutyric acid.
- Alpha-ketobutyric acid results from the breakdown of threonine or methionine during glutathione production.
- Specifically, cystathionine is metabolized to alpha-ketobutyric acid and cysteine.
- a- ketobutyric acid enters the mitochondrial matrix and get converted to propionyl-CoA by the branched chain keto-acid dehydrogenase complex (BCKDHC) and enters the Krebs cycle at succinyl-CoA.
- Evaluate lactate and the branched chain keto acids
- Evaluate alpha-hydroxybutyric acid
- Associated Nutrients: Vitamin B3
- a -Ketobutyric acid is produced from cystine, along with hydrogen sulfide (H2S) as a by-product.
- a- Ketobutyric acid is reversibly converted to a- hydroxybutyric acid.
What does it mean if your 2-OXO-Butyric Acid result is too high?
- Alpha-ketobutyric acid results from the breakdown of threonine or methionine during glutathione production.
- Specifically, cystathionine is metabolized to alpha-ketobutyric acid and cysteine.
- a- ketobutyric acid enters the mitochondrial matrix and get converted to propionyl-CoA by the branched chain keto-acid dehydrogenase complex (BCKDHC) and enters the Krebs cycle at succinyl-CoA.
- Evaluate lactate and the branched chain keto acids
- Evaluate alpha-hydroxybutyric acid
- Associated Nutrients: Vitamin B3
- a -Ketobutyric acid is produced from cystine, along with hydrogen sulfide (H2S) as a by-product.
- a- Ketobutyric acid is reversibly converted to a- hydroxybutyric acid.
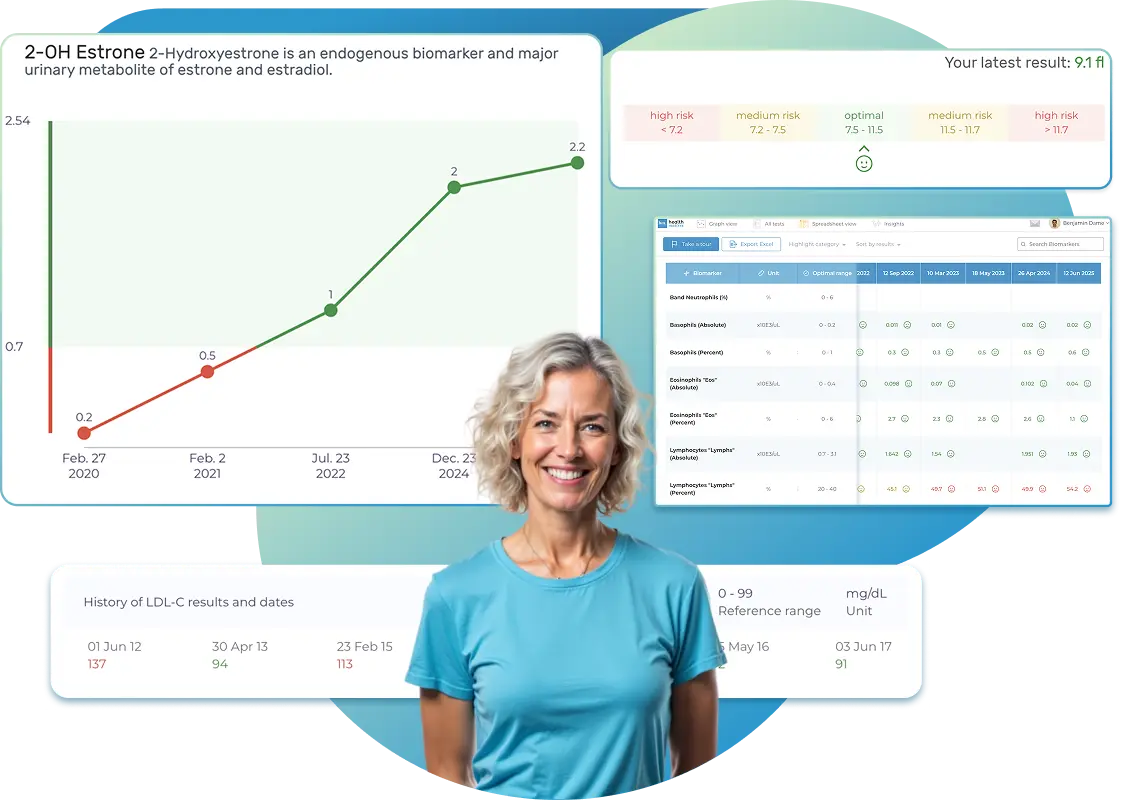
All Your Lab Results.
One Simple Dashboard.
Import, Track, and Share Your Lab Results Easily
Import, Track, and Share Your Lab Results
Import lab results from multiple providers, track changes over time, customize your reference ranges, and get clear explanations for each result. Everything is stored securely, exportable in one organized file, and shareable with your doctor—or anyone you choose.
Cancel or upgrade anytime
Laboratories
Bring All Your Lab Results Together — In One Place
We accept reports from any lab, so you can easily collect and organize all your health information in one secure spot.
Pricing Table
Gather Your Lab History — and Finally Make Sense of It
Finally, Your Lab Results Organized and Clear
Personal plans
$79/ year
Advanced Plan
Access your lab reports, explanations, and tracking tools.
- Import lab results from any provider
- Track all results with visual tools
- Customize your reference ranges
- Export your full lab history anytime
- Share results securely with anyone
- Receive 5 reports entered for you
- Cancel or upgrade anytime
$250/ once
Unlimited Account
Pay once, access everything—no monthly fees, no limits.
- Import lab results from any provider
- Track all results with visual tools
- Customize your reference ranges
- Export your full lab history anytime
- Share results securely with anyone
- Receive 10 reports entered for you
- No subscriptions. No extra fees.
$45/ month
Pro Monthly
Designed for professionals managing their clients' lab reports
- Import lab results from any provider
- Track lab results for multiple clients
- Customize reference ranges per client
- Export lab histories and reports
- Begin with first report entered by us
- Cancel or upgrade anytime
About membership
What's included in a Healthmatters membership
 Import Lab Results from Any Source
Import Lab Results from Any Source
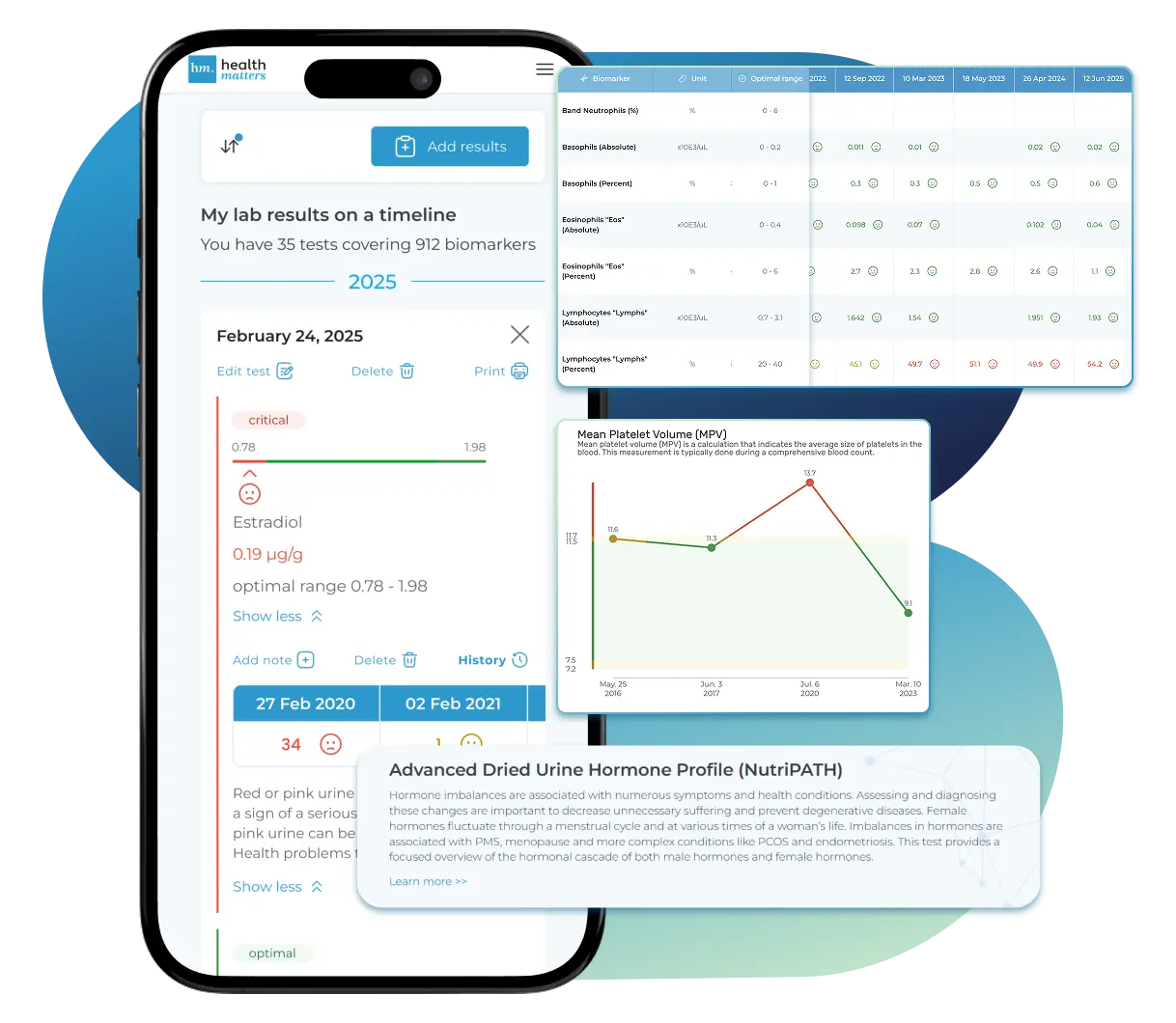
 See Your Health Timeline
See Your Health Timeline
 Understand What Your Results Mean
Understand What Your Results Mean
 Visualize Your Results
Visualize Your Results
 Data Entry Service for Your Reports
Data Entry Service for Your Reports
 Securely Share With Anyone You Trust
Securely Share With Anyone You Trust
Let Your Lab Results Tell the Full Story
Once your results are in one place, see the bigger picture — track trends over time, compare data side by side, export your full history, and share securely with anyone you trust.





Bring all your results together to compare, track progress, export your history, and share securely.
What Healthmatters Members Are Saying
Frequently asked questions
Healthmatters is a personal health dashboard that helps you organize and understand your lab results. It collects and displays your medical test data from any lab in one secure, easy-to-use platform.
- Individuals who want to track and understand their health over time.
- Health professionals, such as doctors, nutritionists, and wellness coaches, need to manage and interpret lab data for their clients.
With a Healthmatters account, you can:
- Upload lab reports from any lab
- View your data in interactive graphs, tables, and timelines
- Track trends and monitor changes over time
- Customize your reference ranges
- Export and share your full lab history
- Access your results anytime, from any device
Professionals can also analyze client data more efficiently and save time managing lab reports.
Healthmatters.io personal account provides in-depth research on 10000+ biomarkers, including information and suggestions for test panels such as, but not limited to:
- The GI Effects® Comprehensive Stool Profile,
- GI-MAP,
- The NutrEval FMV®,
- The ION Profile,
- Amino Acids Profile,
- Dried Urine Test for Comprehensive Hormones (DUTCH),
- Organic Acids Test,
- Organix Comprehensive Profile,
- Toxic Metals,
- Complete Blood Count (CBC),
- Metabolic panel,
- Thyroid panel,
- Lipid Panel,
- Urinalysis,
- And many, many more.
You can combine all test reports inside your Healthmatters account and keep them in one place. It gives you an excellent overview of all your health data. Once you retest, you can add new results and compare them.
If you are still determining whether Healthmatters support your lab results, the rule is that if you can test it, you can upload it to Healthmatters.
We implement proven measures to keep your data safe.
At HealthMatters, we're committed to maintaining the security and confidentiality of your personal information. We've put industry-leading security standards in place to help protect against the loss, misuse, or alteration of the information under our control. We use procedural, physical, and electronic security methods designed to prevent unauthorized people from getting access to this information. Our internal code of conduct adds additional privacy protection. All data is backed up multiple times a day and encrypted using SSL certificates. See our Privacy Policy for more details.
















